
Edgar Cervantes / Android Authority
TL;DR
- Android 15 could introduce a new Enhanced Confirmation Mode that makes it harder for malicious apps to exploit an OS loophole.
- Android blocks users from easily enabling the Accessibility or Notification Listener services of apps that are sideloaded from outside an app store.
- However, the method that Android uses for this has a loophole in it that Android 15 will close.
Although most Android users download apps from preloaded app stores like Google Play, some users get their apps from alternative online sources, a practice called sideloading. This is possible because Android lets users install third-party apps without the Google Play Store so long as they get their hands on the necessary app installation files. The ability to freely sideload apps is a big part of what makes Android a more open platform than iOS. Unfortunately, it’s also the reason why people erroneously believe that Android is less secure than iOS.
That’s because regardless of where you source apps from, Android’s built-in privacy and security features ensure they can’t access sensitive permissions without your consent. However, it’s true that sideloading apps from alternative online sources carries a bit more risk for the average user when compared to sticking with Google Play. This is because it’s simply easier for malicious developers to distribute apps outside of Google Play since they don’t need to deal with the regulations, bureaucracy, and scrutiny that Google Play app distribution entails.
Malicious Android apps, no matter where they’re sourced from, commonly try to trick users into granting them access to the Accessibility and Notification Listener APIs because of their power. The Accessibility API lets apps read the content of the screen and also perform inputs on behalf of the user, while the Notification Listener API lets apps read or take action on any notification. These APIs can be used to commit ad fraud, steal one-time passwords (OTPs), install additional payloads, and do much, much more.
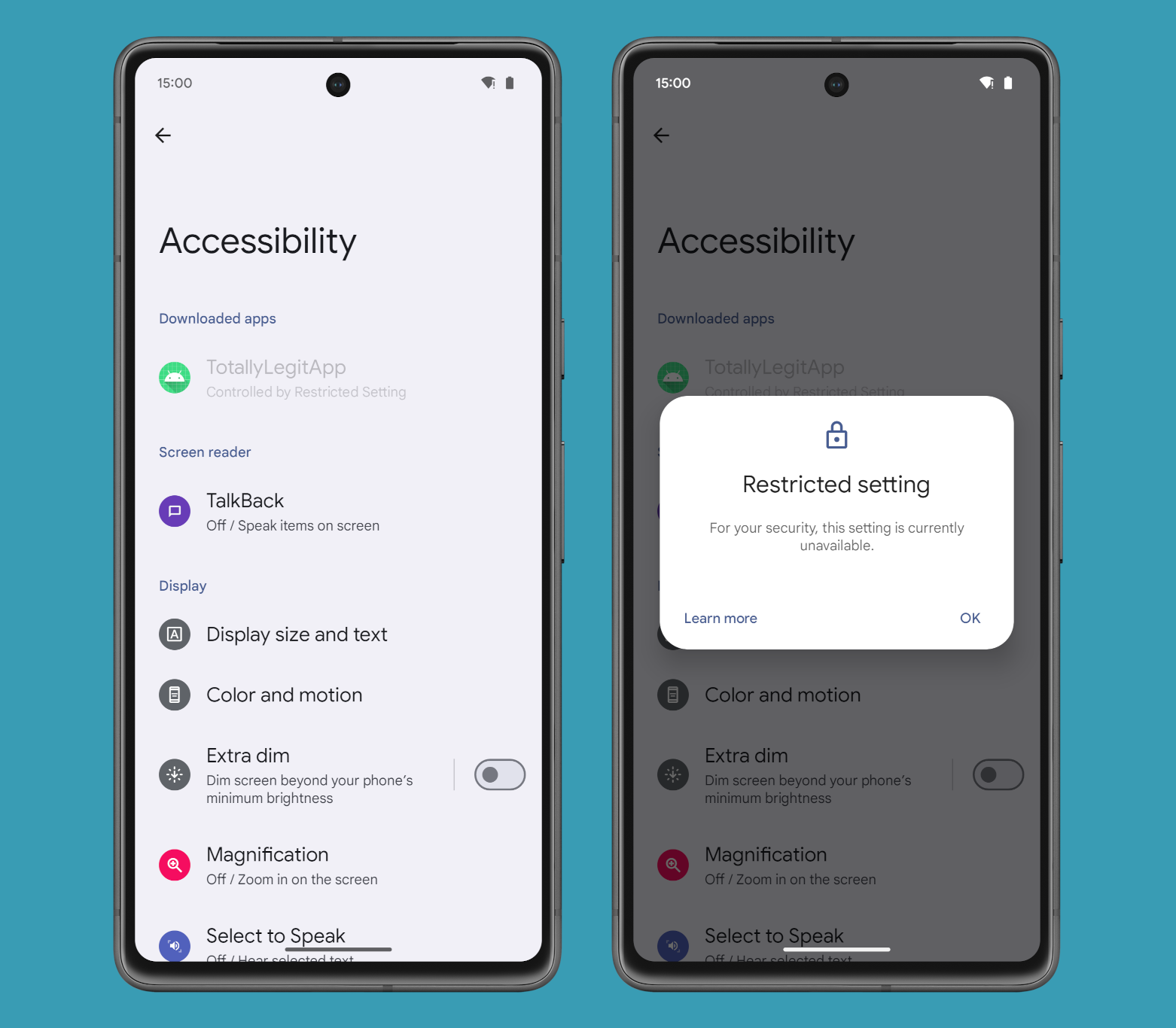
While Google Play has some (mostly bureaucratic) measures to ensure these APIs are used for their intended purposes, Android itself relies mostly on the app’s own declarations to decide how much access to grant. For example, starting in Android 13, the operating system prevents users from easily enabling the Accessibility or Notification Listener services of apps that were sideloaded from outside of an app store. If you were to, say, sideload an app sent to you via email, then Android would block you from enabling that app’s Accessibility or Notification Listener service as they’re marked as “restricted settings.”
Mishaal Rahman / Android Authority
How does the OS know when apps are sideloaded from outside of an app store? It determines this based on whether or not the app that did the installation used Android’s session-based installation APIs (which are commonly but not exclusively used by app stores) versus Android’s non-session-based installation APIs (which are commonly used by file managers, web browsers, and other apps with generic file downloading support). The problem with this approach is that any app can utilize Android’s session-based installation APIs to sideload another app, meaning there’s no guarantee that a legitimate, third-party app store is actually the one that’s doing the sideloading. Malicious app developers have sadly recognized this loophole in Android’s Restricted Settings feature and have already been exploiting it to bypass this security feature.
Fortunately, Google is working on closing this obvious loophole in Android’s Restricted Settings feature. In Android 15, the company is preparing to introduce a new “Enhanced Confirmation Mode” feature that’s basically a tighter, more souped-up version of Restricted Settings. Although the Enhanced Confirmation Mode feature isn’t yet enabled in the latest Android 15 Beta 1.1 update, I analyzed the code and explained how it’ll work in some detail.
For starters, the wording in the Enhanced Confirmation Mode dialog closely matches the existing Restricted Settings dialog. Just like with Restricted Settings, the ECM dialog will say, “for your security, this setting is currently unavailable” when you try to enable an app’s Accessibility or Notification Listener service. However, the dialog will expand on the reasoning a bit by adding that “this app has requested the %1$s permission, which is a restricted setting because it can put your security & privacy at risk. Restriction to this permission may prevent this app from working.” Other than that, the rest of the dialog is the same, down to the title and the two buttons.
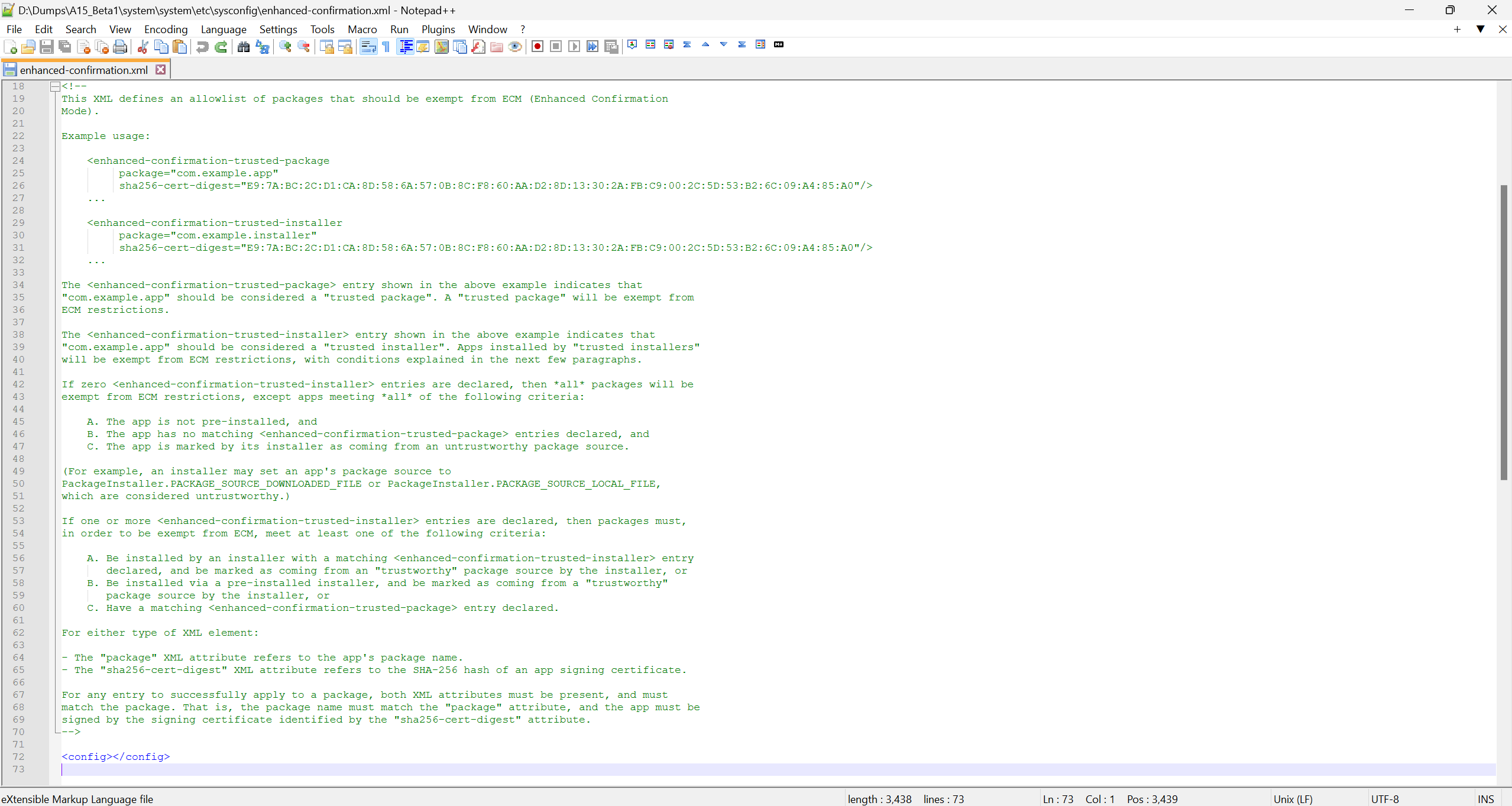
One crucial difference between Android 15’s new Enhanced Confirmation Mode and Android 13’s Restricted Settings feature is how they’re enforced. Instead of differentiating based on what installation APIs were used, Enhanced Confirmation Mode in Android 15 checks an allowlist that’s preloaded in the factory image. This allowlist is an XML file located in the /system/etc/sysconfig path of Android 15, and it determines which packages and installers are exempt from any restrictions.
Mishaal Rahman / Android Authority
Any packages that are explicitly allowlisted in the XML file are considered “trusted packages” and are exempt from ECM restrictions. Similarly, any installers that are listed in the XML file are considered “trusted installers,” which means the apps they then install are eligible to be exempt from ECM restrictions. An app installed by a “trusted installer” is exempt from ECM restrictions if it’s marked as coming from a “trustworthy” package source (i.e., it’s not marked as PACKAGE_SOURCE_DOWNLOADED_FILE or PACKAGE_SOURCE_LOCAL_FILE).
This means that users will be forced to see the Enhanced Confirmation Mode dialog if they try to enable an app’s Accessibility or Notification Listener service, provided the app came from an untrusted installer or an untrusted source. This would effectively close the loophole that existed in Android 13’s Restricted Settings feature, making it harder for malicious third-party apps to gain highly privileged permissions.
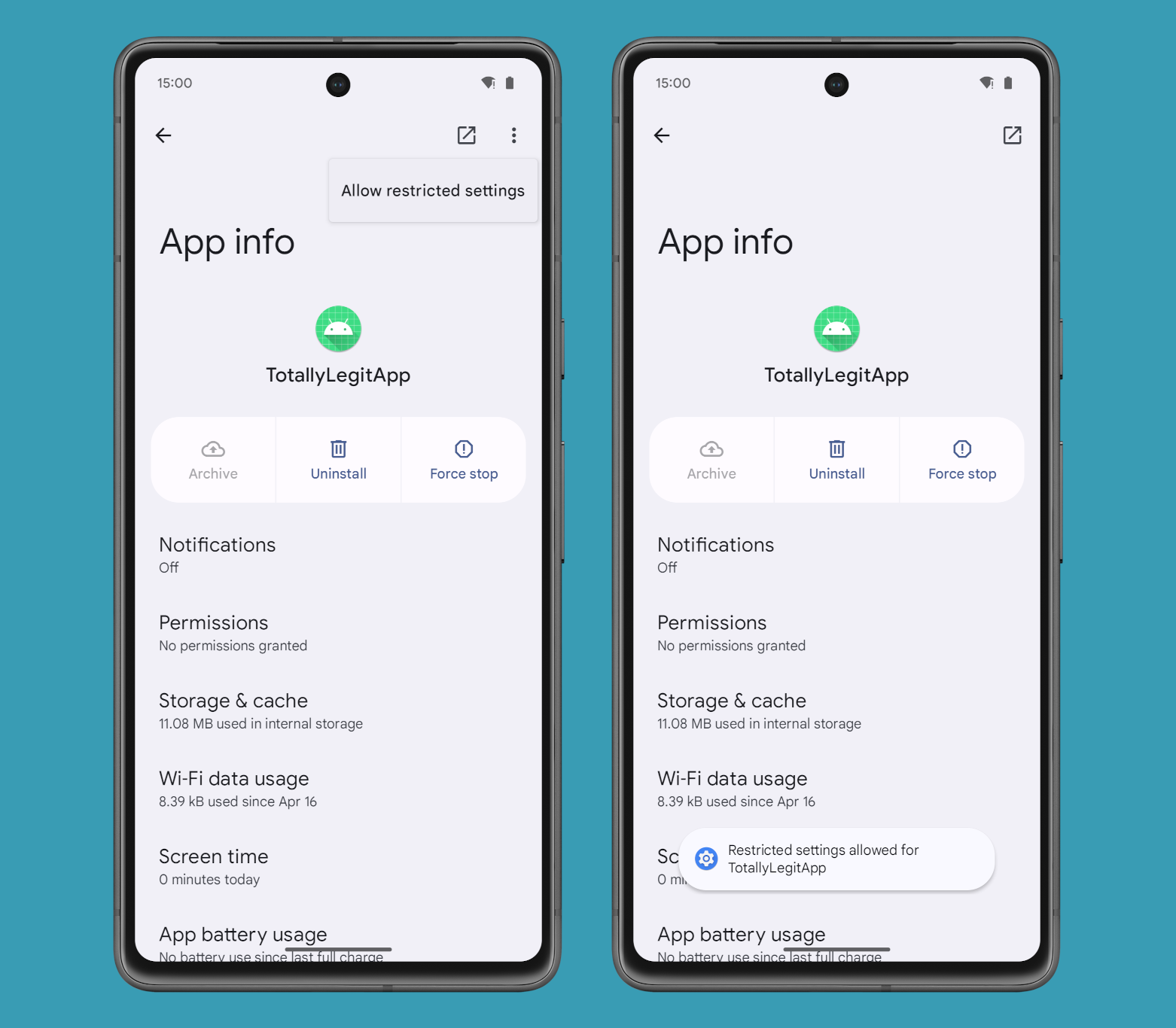
Unfortunately, I’m not sure whether it’ll be possible to still enable a legitimate, sideloaded app’s Accessibility or Notification Listener service if it’s hit with ECM restrictions. It’s possible to disable Restricted Settings for an app, so it should also be possible with ECM restrictions, but I can’t say for sure since I haven’t been able to get the feature to work yet in Android 15.
Mishaal Rahman / Android Authority
It’s also worth noting that currently, zero packages and installers are allowlisted by the system as of Android 15 Beta 1.1. If ECM were enabled, this would mean that all apps would be exempt from ECM restrictions, except those marked as coming from an untrustworthy source. Since ECM isn’t enabled and there aren’t any allowlisted installers or packages, though, I don’t have any information on how Google plans to use this feature. Will Google require the Play Store to be listed as a trusted installer on all Android devices? Which, if any, third-party app stores will Google and OEMs allowlist? These are questions I don’t know the answer to, but regardless, I’m glad to see Google take action to improve security in Android and am looking forward to finding out more details about Enhanced Confirmation Mode in Android 15.
Got a tip? Talk to us! Email our staff at news@androidauthority.com. You can stay anonymous or get credit for the info, it’s your choice.
[ For more curated Samsung, Google, Android news, check out the main news page here]
The post Android 15 may make it even harder for sideloaded apps to get sensitive permissions first appeared on www.androidauthority.com










